Citrix currently has 4 flavors of XenApp (XA) being actively sold on the open market: XenApp Fundamentals for server 2008, XenApp 5 for Server 2003, XenApp 5 for Server 2008, and XenApp 6 for Server 2008 R2. For the most part these all look and feel the same from an end user experience perspective. The value for XenApp in my environment is twofold: managing legacy “problem” applications centrally and providing a secure remote access alternative to traditional VPN for my users. While it’s tempting to jump straight to XA6, my first objective prevents this as many of my problem business applications won’t run on Server 2008 R2 (Windows 7) nor on a 64-bit OS.
Another tool in the Citrix arsenal is application streaming which is the new, and only, version of application isolation. Streaming is available on Advanced, Enterprise, and Platinum versions of XA and there is a special installation method to enable this on Advanced. Streaming is similar to VMware’s ThinApp product where apps are built (profiled) separately on a workstation but published through Citrix. Another advantage is that you can stream directly to the client which will use the client’s hardware resources to run the app taking the load off of the server. Some published limitations exist for streamed apps, however, that include anything requiring special drivers or certain .NET apps.
Planning and design
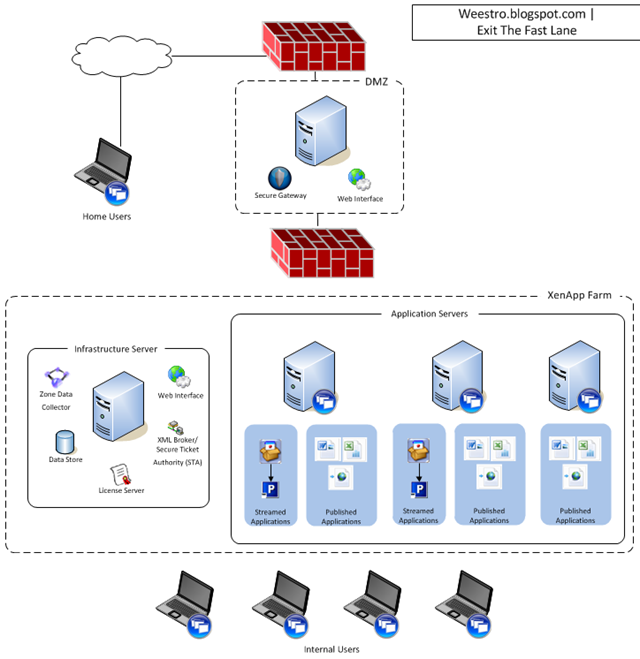
Unlike XA Fundamentals, the full version of the product contains several roles which can all be distributed depending on your environment. The basic server functions in a XA farm are infrastructure servers and application publishing servers. Infrastructure servers handle the functions not related to directly presenting applications to end users. These roles include licensing, data store, zone data collector, web interface, and XML service broker. These roles are well documented and all relate to farm communication and user application presentation. Best practice is to have at least one infrastructure server that will not publish apps to your users and then at least one publishing server. This design model scales easily depending on the size of your organization and performance requirements.

My deployment will consist of 5 servers, all server 2008 R1 x86, all VMs, running on a highly-available ESX4 cluster. 1 x infrastructure server, 3 x publishing servers, and 1 Citrix Secure Gateway (CSG) server. My infrastructure server will host all core roles including the Web Interface (WI) to publish the PNAgent config.xml. Given the size of my organization I have no need to house the data store in a full blown SQL server so I will use the local SQL Express option. Even smaller organizations can use an Access database as well.
My 3 publishing servers will be configured in dual-mode to host both published and streamed apps. 2 of the servers will host identical applications so connections can be load-balanced while the third will be used to host a business application that can only be used with Office 2003. I plan to stream these 2 apps together but I also want to be able to publish these apps externally via a web interface.
My CSG server will be configured to run the gateway and WI for external users to connect to. It will be configured in a single-hop DMZ design. Dual-hop would separate the CSG from the WI on different servers in different DMZs but I don’t have a need to do that now. The firewall will need to be configured to allow the CSG server to talk to each of the publishers via TCP/1494 (ICA), TCP/2598 (session reliability), and TCP/80 for the XML service (optionally configured to use HTTPS). The CSG will also need to be able to talk to the infrastructure server on TCP/80 for XML/ STA (Secure Ticket Authority) services. There is no need to open anything further to the infrastructure server.

Here is the logical architecture for my deployment:
Infrastructure Server Installation
There are plenty of walk-throughs that take you step-by-step through the install process, check out http://www.dabcc.com for some good ones. I want to discuss some of the less documented gotchas that I ran across during my build-out. One of my big complaints with XA5 is the handling of pre-requisites. While this is much improved in XA6, XA5 is pretty painful in this regard depending on which components you install. There are 3 main roles that will be needed on the infrastructure server: terminal services, application server, and web server. My TS licensing is hosted on another server so I only need to install the actual TS component. Please note that EVERY XA server that you turn up, including the infrastructure server, requires terminal services to be installed. Even though your infrastructure server will not be publishing apps, it will be fully capable of doing so. XA cannot be installed without the TS role installed first!
Each component of the XA setup wizard will prompt you for the role services that it needs for the install to complete, but you will have to restart the wizard each time if you are missing anything. To save you the trouble ensure that the following IIS role services are installed before you launch setup (make sure to also enable Windows Authentication under security, not shown):

Optionally add the COM+ Network Access role service to the Application Server role if you want to be able to remotely manage your server from the Access Management Console (AMC):

You will also need the latest x86 JRE installed for the licensing server component. Important to note is that you will need the x86 JRE even on an x64 server!

If you plan to use SQL Express for the data store, go ahead and get this ready now as well because the setup wizard will not do it for you. Run SetupSqlExpressForCPS.cmd in DVDRoot\Support\SqlExpress_2005_SP2. It will instal SQL Express 2005 SP2 and create a database called CITRIX_METAFRAME that the XA setup will look for if you choose the SQL Express installation option. Citrix strongly recommends that you do not install SQL Server on your XA server, only Access or SQL Express.
With those pieces installed you should be good to kick off the XA installer. XA5 doesn’t really break out individual roles like “XML broker” or “zone data collector”, much of it is implied. Such as the first server in a farm automatically becomes the XML broker, STA, and zone data collector. All servers will run the XML Service but only the XML broker will be running IIS which can share the same port. Any of the servers are capable of becoming the Zone Data Collector, controlled via election preferences, which is controlled in the Advanced Configuration tool. If you are installing Advanced Edition and plan to use Application Streaming, you must run the Platinum Edition installer! The server edition will be changed later in the AMC.

Select the Application Virtualization option next which will launch the installer for all common components. On your infrastructure server enable all options, for you publishers all you need is the Access Management Console and XenApp:
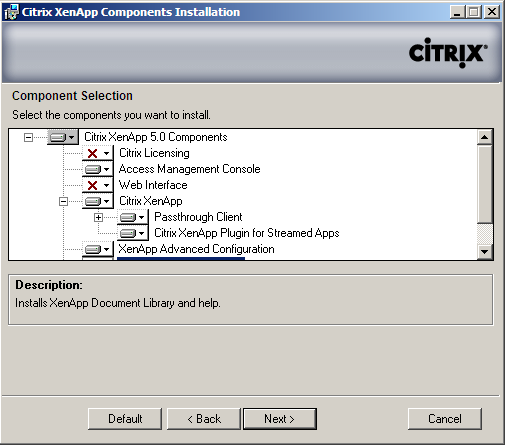
Here is why you run the Platinum installer with the intention of ultimately running Advanced Edition, the Advanced installer does not have this option available:
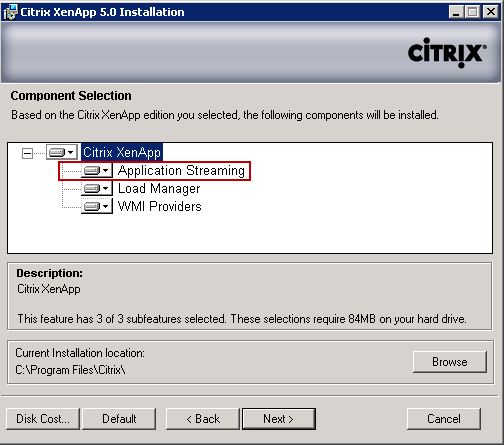
Each component will install separately and can be upgraded individually. This will provide you with the base install. There are 2 additional categories of installables after the base install: hotfixes and feature packs (FP). Hotfixes are provided per OS platform and are installed sequentially, each requiring a reboot. The feature pack, currently FP3 for XA5, includes upgrades to individual server components installed individually, such as the AMC, License server, plugins, Secure Gateway, and WI. Install your required hotfixes then upgrade the individual components included in the FP. You may not need everything in the pack. For Server 2008 R1 x86 I have the following hotfixes installed on each server in my farm. There will eventually be a hotfix rollup that bundles these but not as of this writing. I installed these in order:
XAE500W2K8005.msp
XAE500W2K8017.msp
XAE500W2K8018.msp
XAE500W2K8030.msp
XAE500W2K8042.msp
XAE500W2K8049.msp
Don’t forget to also upgrade the online and offline plugins on all XA servers!
[Advanced only] Once installation is complete and all desired components are updated, launch the AMC, run the discovery process, navigate to your server and set the server edition to Advanced. This will allow proper licensing to work and make your publishers streaming capable:
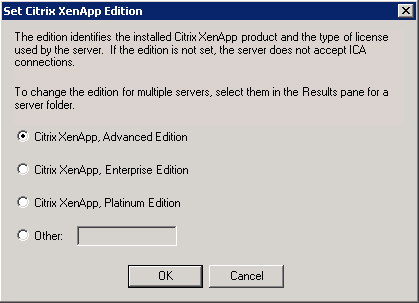
Repeat this process on all XA servers and you’ll be ready to start installing and publishing apps. The first time you run the AMC it will run discovery on the environment, uncheck the Password Manager piece or you will get errors, unless you installed single-sign on with Platinum. The very next thing you should do is create the XenApp Services Site that clients using the online plugin will connect to. Under the Citrix Web Interface Console, right-click the XA Services Site and click create site. Once the PNAgent site is set up, right click it in the WI Console for a number of configuration options. I chose to enable pass-through authentication and made it the default, as well as enabled dual-mode for resource types, for starters. Publishing apps is fairly self-explanatory. Install the on/offline plugins on your client’s PCs and when they are granted access to applications they will see them either in the plugin, the start menu, desktop, or all three.
Citrix Secure Gateway
Both the Citrix Access Gateway (CAG) and Secure Gateway solutions accomplish the same thing, the difference being that the CAG is an appliance (not free) and the CSG (free) runs on a Windows server. The installation process is similar although you can skip right to the latest versions of both the WI and CSG. You will need a valid SSL cert on this server as it will be public facing and accepting only secure connections. When you generate your Cert request (CSR) make sure to choose at least 2048-bits as most CAs are requiring this as a minimum now. This will generate a 256-bit certificate for your site.
My goal was to provide an HTTP redirect to the gateway, so clients can connect to http, as well as host the WI on a TCP port not opened to the world. By default the WI will install into the default IIS site bound to TCP/80. I created a new site, bound to tcp/8080, where the WI would live. I left a single page in the default site that performs a simple redirect to tcp/443. The CSG is the only service that should be listening on this port. Run the WI installer first and create your XenApp Web Site in the new IIS site with port 8080. Once your new certificate is installed on your server you can run the CSG Configuration Wizard. It should find your new cert. Most of the defaults in the configuration wizard can be accepted. You will need to specify your STA server (infrastructure), as well as specify where the WI lives. If you follow my example you will need to tell the CSG that the WI is installed on the same server on TCP/8080.

Make sure to set up your WI site properly with your farm info and the appropriate secure access method. Direct is the simplest unless you’re using NAT between your DMZ and inside networks in which case you’d use gateway alternate or gateway translated. Customize your WI appearance how you like and assuming all firewall changes are in place you should now be able to access the WI externally.
At a high-level that’s it for my architecture. Citrix is a deep well and there are obviously a ton of other options and features that one could deploy. Another consideration worth pondering is user profiles. Citrix recommends using roaming TS profiles centrally stored on NAS or SAN to ensure a consistent user experience. This is easily enforced via GPO which I have employed and it works well. In combination with folder redirection this provides a very solid solution for managing your Citrix resources.
While it is ok to mix x86 and x64 servers in your XA farm, consider the implications this will have on program installations and user profiles. Published apps are defined via paths to their executables so if these paths are not the same on all of your servers you will have to make special concessions (c:\program files vs c:\program files (x86)). There are also additional differences in appdata folders used by some applications for x64 or x86 platforms. Many have had luck using the Flex Kit for managing profiles in these environments.
Although not cheap, XenApp 5 provides a very slick application delivery solution. XA5 Advanced costs in the neighborhood of $250/CCU and you also need to buy TS CALs as well. Enterprise and Platinum Editions increase costs significantly. The basic RemoteApp functionality baked into Server 2008 works well but at the sacrifice of granular presentation management, detailed performance tuning, and easy scalability. Citrix doesn’t care how many servers you put in your farm or what roles you run where, it’s all about the CCU licenses. Citrix and Microsoft have a very cohesive relationship going way back so XenApp will integrate seamlessly into your environment. One thing to watch out for is XenApp component changes to your servers after installation. I’ve noticed some finicky behavior specifically with regard to the license server component and having to reinstall it to get it working correctly again.
Resources:
Application Streaming with XenApp Advanced


0 Comments