The Cisco AnyConnect 2.5 client in conjunction with ASA ASDM version 6.3 bring several new features to Cisco’s SSL VPN implementation. Some of the more interesting features are:
- Post Log-In Always-on VPN – VPN session is auto-established after user logs into PC.
- Connect Failure Policy – Determines if user is allowed to access internet if Always-On VPN is enabled and AnyConnect cannot establish VPN session.
- Captive Portal Hotspot Detection/Remediation – Detects “pay for internet access” types of portals seen in hotels or airports and allows users timed access to establish connectivity.
- Quarantine – Restricts client PCs that are out of compliance and allows remediation options (AV updates, etc).
- AnyConnect Profile Editor – Provides GUI-based profile editing via ASDM instead of XML-only editing.
Here is my setup:
- 2 x ASA 5510’s in active/active cluster
- ASA version: 8.2(1)
- ADSM version: 6.3(1)
- Security Plus license
- AnyConnect Essentials license (total VPN peers: 250)
Building the client profiles is easy enough, in ASDM you just select the Remote Access VPN tab and drill down to AnyConnect Client Profile under Network (client) Access. Select Add, give the profile a name, and configure your policy.
Once the XML file is created on the ASA you can set your policy options:

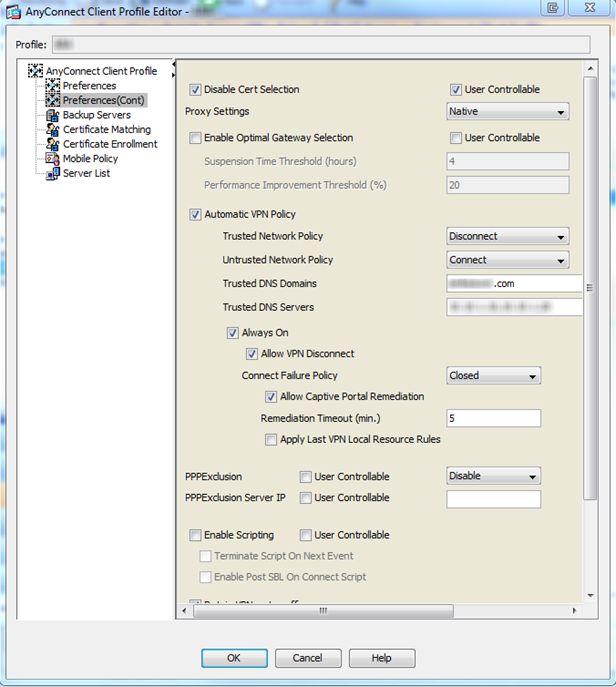
The Always on piece is set on the Preferences(Cont) page. Here you can get really restrictive by having the AnyConnect client detect the PC’s network state and apply actions based on it. If the client detects a trusted network (defined in the profile), VPN will disconnect, if the network is untrusted it will connect (Trusted Network Detection/TND). You can allow or disallow disconnection of the VPN session by the user and set a connect failure policy. When the connect failure policy is set to closed the user will be unable to even browse the internet from their home network unless VPN is established. Setting to Open reverses this behavior. If you build split tunnels into your group policy then only traffic destined to the specified corporate resources will flow over the VPN tunnel. Anything internet related can go out whatever internet connection they are connected to. You can, of course, force all traffic over the VPN tunnel.
The part where this breaks is when you attempt to assign the profile to a group policy via ASDM[unless, as someone pointed out in the comments, you are running ASA 8.3(1)]. This screenshot actually shows the correct sequence of commands being executed although I have seen it try to apply the profile from the global webvpn sub menu. In any case this has not worked for me through ASDM after multiple attempts with different profiles and group policies [because I am on ASA version 8.2(1)].

Assigning your ASDM-configured client profile via the ASA CLI works fine. ADSM is essentially trying to do the same thing but it just doesn’t work [for me].
1) Register the client profile XML as a global profile package:
ASA1(config)# webvpn
ASA1(config-webvpn)# svc profiles TestProfile disk0:/TestProfile.xml
ASA1(config-webvpn)# exit
2) Confirm the package is available to the group policy “VPN_GroupPolicy”:
ASA1(config)# group-policy VPN_GroupPolicy attributes
ASA1(config-group-policy)# webvpn
ASA1(config-group-webvpn)# svc profiles value ?
config-group-webvpn mode commands/options:
Available configured profile packages:
TestProfile
3) Assign the profile package to the group policy:
ASA1(config-group-webvpn)# svc profiles value TestProfile
Once the user logs into the appropriate group on their AnyConnect client they will pull down the profile XML which gets stored in c:\ProgramData\Cisco\Cisco AnyConnect VPN Client\Profile. Per the enabled settings above this is what the client state looks like in a trusted and untrusted network:
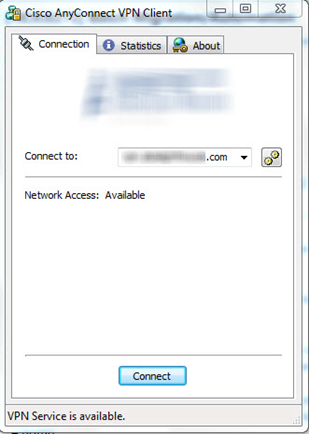
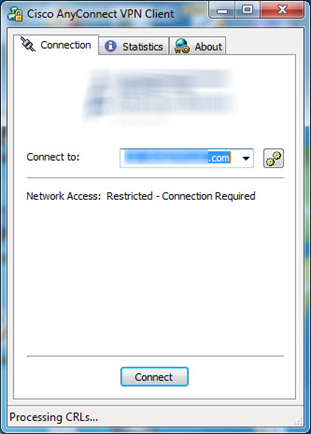
As you can see the result of the closed Connect Failure Policy on the right, the user will have to establish VPN before being allowed to even get out to the internet on a home or public network.
Microsoft has a similar solution with their DirectAccess implementation. DirectAccess abilities are built into Windows 7 Enterprise and Ultimate so require no additional clients. I started to go down that road first but got scared away by the list of requirements and infrastructure changes I would have to make on the backend to implement. AnyConnect is an excellent alternative that comes with the peace of mind of Cisco security plus there is no additional infrastructure to set up. SSL VPN is not free, however, and comes in two flavors: premium and essentials. The essentials license for my 5510 cluster, which supports a max of 250 VPN peers, was under $100. Premium lics are several times more expensive.
*It should be noted that if you intend to upgrade your ASA to 8.3(1) then you may need to also increase the amount of DRAM in your appliance. Cisco upped the default amount in all devices purchased after Feb 2010. Link.
*A quick note about TND, it can indeed be spoofed. The 2 criteria that the AC client is looking for is the trusted domain name and DNS server address list. If you configure these 2 items to match what is expected in the AC client profile, the AC client will think the network is trusted. If you change or add DNS servers to your corporate DHCP server scopes, this will break TND. The AC client profile must match what is given to the client via DHCP (or statically) for this to work.
Here is my client profile XML, for reference:
<?xml version="1.0" encoding="UTF-8"?>
<AnyConnectProfile xmlns="http://schemas.xmlsoap.org/encoding/" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://schemas.xmlsoap.org/encoding/ AnyConnectProfile.xsd">
<ClientInitialization>
<UseStartBeforeLogon UserControllable="false">false</UseStartBeforeLogon>
<AutomaticCertSelection UserControllable="true">false</AutomaticCertSelection>
<ShowPreConnectMessage>false</ShowPreConnectMessage>
<CertificateStore>All</CertificateStore>
<CertificateStoreOverride>false</CertificateStoreOverride>
<ProxySettings>Native</ProxySettings>
<AutoConnectOnStart UserControllable="true">true</AutoConnectOnStart>
<MinimizeOnConnect UserControllable="true">true</MinimizeOnConnect>
<LocalLanAccess UserControllable="true">true</LocalLanAccess>
<AutoReconnect UserControllable="false">true
<AutoReconnectBehavior UserControllable="false">ReconnectAfterResume</AutoReconnectBehavior>
</AutoReconnect>
<AutoUpdate UserControllable="false">true</AutoUpdate>
<RSASecurIDIntegration UserControllable="false">Automatic</RSASecurIDIntegration>
<WindowsLogonEnforcement>SingleLocalLogon</WindowsLogonEnforcement>
<WindowsVPNEstablishment>AllowRemoteUsers</WindowsVPNEstablishment>
<AutomaticVPNPolicy>true
<TrustedDNSDomains>domain.com</TrustedDNSDomains>
<TrustedDNSServers>10.10.10.10,20.20.20.20</TrustedDNSServers>
<TrustedNetworkPolicy>Disconnect</TrustedNetworkPolicy>
<UntrustedNetworkPolicy>Connect</UntrustedNetworkPolicy>
<AlwaysOn>true
<ConnectFailurePolicy>Closed
<AllowCaptivePortalRemediation>true
<CaptivePortalRemediationTimeout>20</CaptivePortalRemediationTimeout>
</AllowCaptivePortalRemediation>
<ApplyLastVPNLocalResourceRules>false</ApplyLastVPNLocalResourceRules>
</ConnectFailurePolicy>
<AllowVPNDisconnect>true</AllowVPNDisconnect>
</AlwaysOn>
</AutomaticVPNPolicy>
<PPPExclusion UserControllable="false">Disable
<PPPExclusionServerIP UserControllable="false"></PPPExclusionServerIP>
</PPPExclusion>
<EnableScripting UserControllable="false">false</EnableScripting>
<EnableAutomaticServerSelection UserControllable="false">false
<AutoServerSelectionImprovement>20</AutoServerSelectionImprovement>
<AutoServerSelectionSuspendTime>4</AutoServerSelectionSuspendTime>
</EnableAutomaticServerSelection>
<RetainVpnOnLogoff>true
<UserEnforcement>AnyUser</UserEnforcement>
</RetainVpnOnLogoff>
</ClientInitialization>
<ServerList>
<HostEntry>
<HostName>ac.domain.com</HostName>
<HostAddress>ac.domain.com</HostAddress>
</HostEntry>
</ServerList>
</AnyConnectProfile>


0 Comments