One of the problems that has continued to plague Windows is the ability for users, administrative or not, to execute programs from unsafe temporary file system locations sometimes bypassing security controls. UAC has helped to reduce the attack surface along with the Windows integrity mechanism that monitors and restricts files based on a level of trustworthiness. Combine that with a good anti-virus product and sometimes the bad stuff can still get through, even when accidentally executed from a dangerous location such as temporary internet files. Internet Explorer contributes to this problem as the only major browser on the market that actually allows execution directly from a download (which can happen accidentally). Chrome and Firefox require a download to be saved to disk first then manually executed after the download is completed. This alone is good enough reason to not use IE for daily casual browsing.
Microsoft’s AppLocker is a free built-in group policy utility that comes with the Enterprise and Ultimate versions of Windows that puts a stranglehold on the execution environment of the OS. Unlike the troublesome software restriction policies of long ago, AppLocker provides an intuitive and highly customizable framework to protect your PC and servers, if desired. AppLocker works for home or corporate PCs and can be configured using group policy. I have configured AppLocker on every Win7 PC I’ve built for friends or family for years and they do not have malware problems. Period.
Best practices for novice or intermediate user PCs:
- Users should not run as administrators, remove the user account from local admins
- Enable the local admin account and set a password
- Run a quality antivirus product
- Ensure UAC is enabled and set to the default level
- Configure AppLocker to protect the OS
Accessed from within the local computer security policy (gpedit.msc) or via group policy in a AD domain, AppLocker can be found in the Application Control Policies section below Security Settings.
A number of different rule types can be configured and new for Win8/ Server 2012, AppLocker now supports Packaged apps, which I’ll talk about in the section that follows.
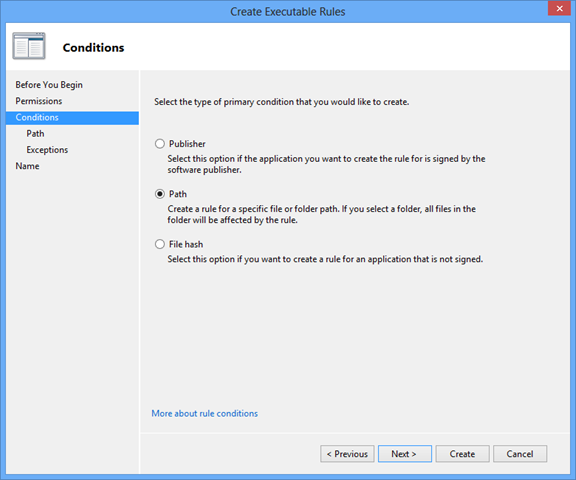
Executable Rules
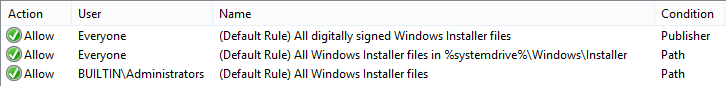
Executable rules are by far the simplest and most effective means of providing solid protection. First thing to do is to create the default rules: right-click in the white space in the right pane, click “create default rules.” These rules will ensure that executables can only be run from within the trusted program files and windows folders. Administrators will be allowed to execute any file regardless of file system location. Anything that is executed from the desktop or temp folders, for example, will be denied.
For the PC of a non-administrative user, to execute a file outside of the specified safe locations will require both intent and elevation via UAC to run; no accidents will be possible.
Applications that are not installed for “all users” of a PC are typically installed to a space in %userprofile%\AppData. These applications will need to be individually permitted or they will subsequently fail to run. The easiest method providing the best protection is to configure path rules for each application as required.
If this is too troublesome, a publisher rule will suffice which will cast a wider net allowing any application of a given publisher or product to execute. Move the slider to enforce more or less granularity as desired.
Windows installer and script rules can also be used to to provide further restrictions. Use care if you choose to enable these as frustration could ensue when trying to install certain applications afterwards.
Packaged App Rules
For Windows 8 and Server 2012, having the interface formerly known as Metro and apps to go with it, AppLocker provides a new mechanism to comprehend these “packaged apps.” The options are more limited but provide suitable protection and control.
Create a packaged app rule by first choosing a reference file from the Metro apps installed:
Adjust the slider to specify a publisher, package or version rule:
Enforcement
Any configured rules will be enforced by default unless you specify Audit Only in the enforcement properties.
For any configured rules to actually take affect, the Application Identity service must be running. Set the service to Automatic and start it.
Follow these recommendations and you should never have to clean another malware infested PC again. I honestly can’t remember the last time I’ve had to.
References:










0 Comments