
News Summary
- Cisco Talos discovered a new malicious campaign using a leaked version of Cobalt Strike in September 2021.
- This shows that Cobalt Strike, although it was originally created as a legitimate tool, continues to be something defenders need to monitor, as attackers are using it to set up attacks.
- The threat actor in this case uses domain fronting with the Cloudflare Content Delivery Network, redirecting a Myanmar government owned-domain to an attacker-controlled server.
- The threat actor employed the tactic of re-registering reputed domains in their attack chains to evade detections.
- This threat demonstrates several techniques of the MITRE ATT&CK framework, most notably T1202 - Indirect Command Execution , T1027 - Obfuscated Files or Information, T1105 - Ingress Tool Transfer, T1071.001 - Application Layer Protocols:Web Protocols.
What's New?
Cisco Talos discovered a malicious campaign using an obfuscated Meterpreter stager to deploy Cobalt Strike beacons in September 2021. The actor used a domain owned and operated by the Myanmar government, the Myanmar Digital News network, as a domain front for their beacons.
The evolution of this threat indicates that the attackers have been active since at least August 2021 using a combination of Meterpreter stagers and Cobalt Strike beacons to establish presence on victim's endpoints.
How did it work?
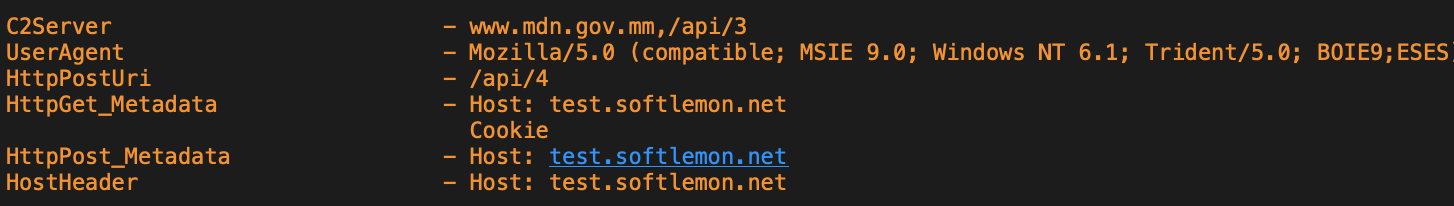
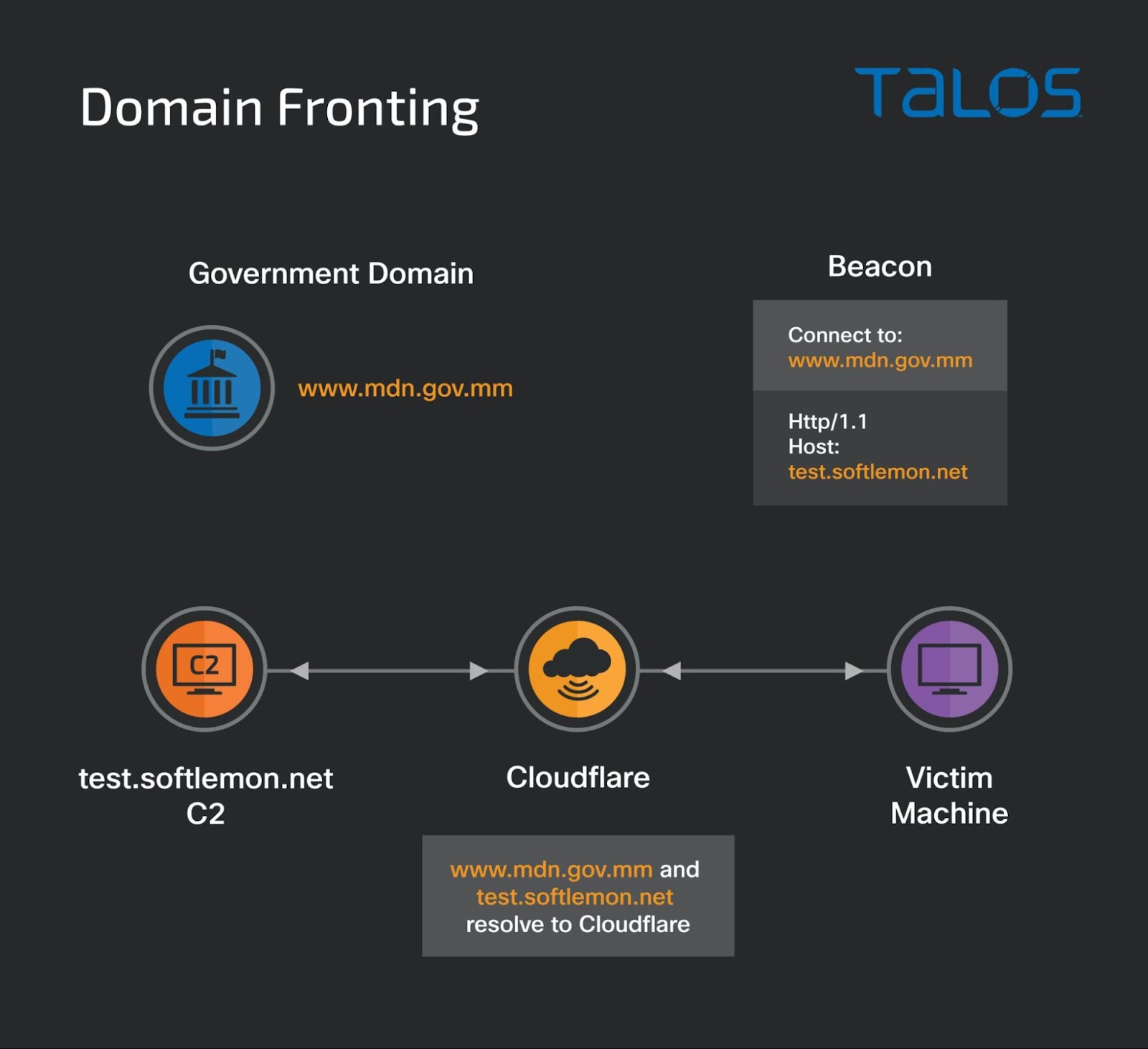
The malware is typically a loader that runs on a victim machine, decodes and executes the Cobalt Strike beacon DLL via reflective injection. It loads several libraries during the runtime and generates the beacon traffic according to the embedded configuration file. The configuration file contains the information related to the command and control (C2) server which instructs the victim's machine to send the initial DNS request attempting to connect to the host of the Myanmar government-owned domain www[.]mdn[.]gov[.]mm. The site is hosted behind the Cloudflare content delivery network and the actual C2 traffic is redirected to an attacker controlled server test[.]softlemon[.]net based on the HTTP host header information specified in the beacon's configuration data.
So what?
Cobalt Strike has been used by many actors in the past and is a de-facto standard tool for post-exploitation activities and pivoting. Attackers use it to deploy a wide range of payloads, from commodity malware, to sophisticated state-sponsored activities.
Cobalt Strike allows actors to shape the traffic of beacons to mimic legitimate traffic patterns. One of the techniques to conceal the traffic from DNS-based filtering is Domain Fronting. Domain fronting uses legitimate or high-reputation domains to remain undetected by defenders. The attacker's choice of Myanmar-specific domains for domain fronting may indicate an interest in the geopolitics of this area of the world.
In this campaign, the actor used staged payloads using the Meterpreter stager, which gives an indication that the beacon will be used for further attacks. The defenders should be constantly vigilant and monitor network traffic to detect Cobalt Strike activities, since it is one of the most commonly used offensive tools by crimeware and APT operators.
Evolution of the campaign
A study of the evolution of the campaign shows the actor experimenting with different combinations of hosts with the intent of perfecting the domain fronting technique.
The earliest beacon discovered around the middle of August 2021 contains the C2 URI set to test[.]softlemon[.]net while the HTTP Get and Post requests headers are pointing to dark-forest-002[.]president[.]workers[.]dev which is a Cloudflare serverless workers domain. The default host header configuration for request contains the host name test[.]softlemon[.]net, which is also used by more recent samples.
Another sample discovered in late August 2021 consisted of the C2 host URI xxx[.]xxxx[.]tk and the host header setting configured to point to test[.]softlemon[.]net.
Beginning September 2021, the attackers started using the Myanmar Digital News domain for fronting their beacons. While the default C2 domain was specified as www[.]mdn[.]gov[.]mm, the beacon's traffic was redirected to the de-facto C2 test[.]softlemon[.]net via HTTP Get and POST metadata specified in the beacon's configuration.
The actor likely changed the configuration to test their infrastructure and the domain fronting functionality before launching the attack. Based on the beacon configuration template and the real C2 host test[.]softlemon[.]net, we assess with moderate confidence that the samples are created by a single actor.
Cobalt Strike beacon configurations
We extracted the beacon config from the payload that showed us the actor has used different values for the User Agent, C2-Server and Host-header in different malwares of this campaign.
The beacon configuration of samples usually has a User Agent, which is Mozilla compatible and of Windows 7.
Watermark
The Cobalt Strike watermark is a number generated from the license file and is unique to a Cobalt Strike license. The watermark on the beacons used in this campaign was 305419896 (hex: 0x12345678).
This particular watermark has previously been attributed to a leaked Cobalt Strike version and is unsurprisingly used by other malicious actors, such as Maze ransomware and Trickbot groups, making attribution based on the watermark number impossible. It is difficult to assess if the usage of the previously registered expired domain for C2 server and the leaked Cobalt Strike point to an increased operational security awareness of the actor or to limited resources available to them.
Domain fronting
The actor in this campaign has used domain fronting, which is a technique which can use high reputation domains to conceal the Cobalt Strike command and control traffic. A government domain of Myanmar www[.]mdn[.]gov[.]mm was used in this particular instance.
The fronted domain mdn[.]gov[.]mm is a legitimate domain of Myanmar Digital News, a state-owned digital newspaper. This website has previously been compromised in February by the Brotherhood of Myanmar group, a collection of militia groups. Although there are no indications that the previous defacement of the domain by the Brotherhood of Myanmar and the campaign described in this post are related, the domain itself is clearly of interest to various actors.
Domain fronting can be achieved with a redirect between the malicious server and the target. Malicious actors may misuse various content delivery networks (CDNs) to set up redirects of serving content to the content served by attacker-controlled C2 hosts. Cloudflare is one of the CDN services that provides its users with a globally distributed cache for files hosted on their servers. Cloudflare identifies distributions by the FQDN used to request resources. Cloudflare users have the option to use their own subdomain and create a DNS record that points to Cloudflare. This subdomain tells Cloudflare to associate that DNS record with a specific distribution.
The beacon calls home www[.]mdn[.]gov[.]mm,/api/3 and has set the Host header to the actual C2 server test[.]softlemon[.]net. The beacon traffic resolves to a Cloudflare IP address. The DNS request that led them there will be lost and relies on other parts of the HTTP request, including the Host header and the actual C2 test[.]softlemon[.]net.
Cobalt Strike payload
The beacons are of particular interest due to the domain fronting technique using a government host as the initial DNS lure. The MITRE ATT&CK framework techniques used by this malware are:
- T1202 - Indirect Command Execution
- T1027 - Obfuscated Files or Information
- T1105 - Ingress Tool Transfer
- T1071.001 - Application Layer Protocols:Web Protocols
We also analysed the loader binary to find specifics of its memory loading and functionality.
We spotted a suspicious section .kxrt with the packed and encoded malicious code. The malware links several functions at runtime and has the Meterpreter staging code.
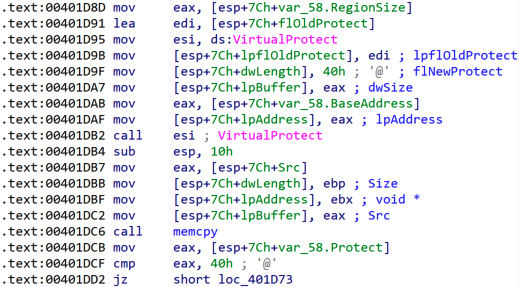
When the malware runs, the .tls section runs first, loads the libraries and starts the execution of the malicious code at the entry point in the .kxrt section. The entry point code calls a function to allocate virtual memory in its own process space.
The loader next calls the VirtualProtect function to set the virtual memory page permissions to Read-Write-Execute and writes the image base of the Cobalt Strike beacon which will be executed in a new thread.
We spotted two libraries linking during runtime. Aside from this, there are several other standard libraries the malware links during the runtime.
After allocating the virtual memory and setting the page permissions to Read-Write-Execute, a decryption routine is executed that decrypts the remaining malicious code in the .kxrt section and writes it to the virtual memory.
The decrypted malicious code is the actual Cobalt Strike beacon. Once decoded, the loader's execution jumps to the beginning of the DLL resulting in a reflective-load of the beacon into the loader process memory. This beacon is now responsible for decoding the configuration.
The beacon resolves the proxy by calling WinHTTPGetProxyForUrlEx and WinHTTPCreateProxyResolver to bypass the proxy for the URL.
Soon after that, the beacon initiates the Cobalt Strike beacon traffic to the C2 server. The DNS request for the initial host resolves to a Cloudflare-owned IP address that allows the attacker to employ domain fronting and send the traffic to the actual C2 host test[.]softlemon[.]net, also proxied by Cloudflare.
At the time of analysis, the sample C2 host infrastructure was not online and we received a 404 error.
The beacon contains techniques to detect debuggers using GetTickCount, IsDebuggerPresent and the NtDelayExecution call to delay the execution of the malware for evading sandbox-based dynamic analysis systems. The beacon can also manage the system power policies registry keys to set the minimum and maximum sleep times and the lid open and close action policy.
Command and control
The C2 server - test[.]softlemon[.]net is the subdomain of softlemon[.]net. The domain softlemon[.]net was registered under Google domains until August 2019 and likely expired since then. The malicious actor re-registered this domain on Aug. 5, 2021. The SSL certificate for the domain softlemon[.]net with the serial number 4aa6af6d719bfdd1c6dff3d7b640aed7ee3was issued by Let's Encrypt, a free SSL certificate provider.
The Talos reputation engine has classified it as an untrusted domain and Cisco Umbrella shows a spike in the DNS queries in September 2021. This activity is consistent with the evolution of the Cobalt Strike beacons illustrated earlier the attackers started instrumenting beacons fronted with the Digital News domain at the beginning of September.
Our research uncovered that the C2 test[.]softlemon[.]net is a Windows server running Internet Information Services (IIS).
According to Shodan, the IP address 193[.]135[.]134[.]124 hosted by a Russian provider may be the real C2 IP address protected by the Cloudflare infrastructure as the SSL certificate served on port 8443 belongs to Cloudflare and lists the X509v3 Subject Alternative Name as DNS:*.softlemon.net.
Conclusion
Domain fronting is a technique used by attackers to circumvent protection based on DNS filtering. In this campaign, a malicious Cobalt Strike beacon is configured to take advantage of a mechanism used by Cloudflare and other content distribution networks to instruct the proxy about the host to be used for serving the content.
When the beacon is launched, it will submit a DNS request for a legitimate high-reputation domain hosted behind Cloudflare infrastructure and modify the subsequent HTTPs requests header to instruct the CDN to direct the traffic to an attacker-controlled host.
Defenders should monitor their network traffic even to high reputation domains in order to identify the potential domain fronting attacks with Cobalt Strike and other offensive tools. XDR tools should be deployed to endpoints in order to detect behavior of Cobalt Strike loaders and Meterpreter stagers as they are frequently used by a wide range of actors.
Coverage
Ways our customers can detect and block this threat are listed below.Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
Cisco Secure Malware Analytics (formerly Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
Umbrella, Cisco's secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs and URLs, whether users are on or off the corporate network. Sign up for a free trial of Umbrella here.
The following ClamAV signatures have been released to detect this threat:
Win.Backdoor.CobaltStrike-9909816-0
Open Source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
IOCs
Hashes
658d550322cefa6efc51fbfd1a3e02839d1e519a20f8f17f01c534c0eaf36f27e806e55713b9e46dc7896521ffb9a8b3abaa597147ea387ff2e93a2469546ba9
a0aec3e9cb3572a71c59144e9088d190b4978056c5c72d07cb458480213f2964
Network IOCs
Hosts
test[.]softlemon[.]netdark-forest-002.president[.]workers[.]dev
IP addresses
193[.]135[.]134[.]124URLs
hxxp://test[.]softlemon[.]net:8081/api/3hxxp://test[.]softlemon[.]net/
tcp://test[.]softlemon[.]net:8080/
hxxps://193[.]135[.]134[.]124:8443
hxxp://193[.]135[.]134[.]124:8080
hxxp://193[.]135[.]134[.]124:8081














0 Comments