By Matt Olney.
- An unpredictable and largely unknown set of actors present a threat to organizations, despite their sometimes unsophisticated techniques. Customers who are typically focused on top-tier, state-sponsored attacks should remain aware of these highly motivated threat actors, as well.
- Misattribution of these actors carries the risk of nations escalating an already dangerous conflict in Ukraine.
- Based on data from our fellow researchers at Cisco Kenna, customers should be most concerned about threat actors exploiting several recently disclosed vulnerabilities, highlighting the importance of consistently updating software and related systems.
- With this rising and diverse threat, we recommend defenders continue to employ security fundamentals, patch aggressively, and leverage finished intelligence reports or other sources to enhance their understanding of the threat landscape.
Each of us, in the face of an unjustified outrage, will look to try and help – but some of these efforts carry the risk of escalating an already dangerous situation. For those of us at Talos, helping has meant standing beside our partners and customers in Ukraine, long nights and weekends looking at telemetry and consoles, and hours of examining the individual instructions of malware deployed in Ukraine. As we monitored the intelligence in the region, we started to see groups assemble who intended to attack critical infrastructure – either in Ukraine or in Russia.
Conti announcement of support for the Russian Federation.
Our unprecedented level of concern at this moment is complicated by a rapidly changing cyber threat landscape that involves actors of all skill levels. In recent days, the Conti ransomware gang — a longtime, familiar foe — warned that it would attack anyone who attempts to interfere with Russia’s invasion of Ukraine. Conti has been split with internal strife, as some members who disagree with the group's stance have started to leak critical intelligence about the group, while multiple new Telegram channels have popped up looking to coordinate attacks against both sides. There’s also movement amongst Ukraine supporters and defenders, as the country’s cyber police have posted online about how they and “volunteers” have targeted the infrastructure of the “occupiers.” We’re also seeing low-level activity from Ukraine sympathizers who have formed a so-called “IT Army” and well-known hacktivist group Anonymous, who declared cyberwar on Russia.
From our perspective, this sudden appearance of many different highly motivated actors of wildly differing levels of capability presents a special hazard given the current political environment. Even low-capability actors have a possibility of getting lucky, and if they get lucky in the wrong place, real-world consequences could come into play. These groups may be mistaken for state-sponsored organizations, without understanding what kind of reactions they might trigger. This is our greatest concern, that the response to a misattributed attack will lead to an escalation in the conflict.
It is important that every organization understands that the general threat level of the Internet at large has risen. A lot of people are feeling righteously angry right now, and that leads some to make bad decisions. From a defender’s perspective, this means paying attention to the fundamentals and not being the low-hanging fruit. This starts with patching, and looking at CISA’s Known Exploited Vulnerabilities Catalog and ensuring that those are prioritized.
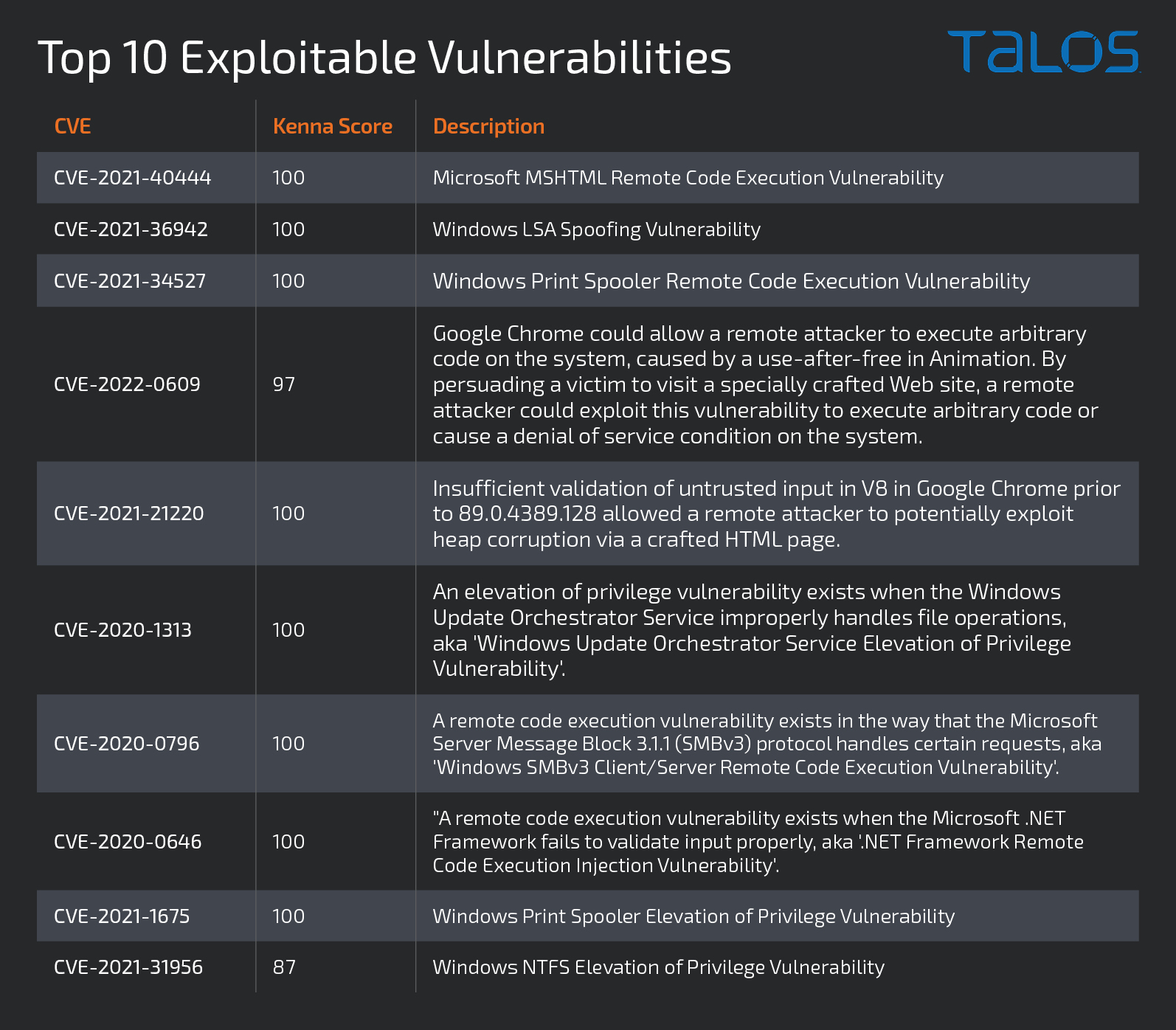
Additionally, we asked our fellow researchers in Cisco’s Kenna group to identify the top 10 vulnerabilities they are worried about threat actors exploiting. As seen in the list below, the vulnerabilities are recent, with the oldest one coming from 2020, and concentrated on Windows and Chromium security flaws.
The threat landscape is changing very quickly. While currently, groups appear to be targeting systems either in Russia or Ukraine, there is nothing saying that the targets will not change to include more countries and industries, particularly as Russia starts to feel the effects of unprecedented sanctions. Take the time now to do a basic security hygiene check, look at your organization from the outside, and try to understand where you need to improve.
In addition to aggressively patching, one of the areas that we are pushing with our customers is an aggressive intelligence collection operation. Again, things are moving very quickly. and being able to extract information from vendor blogs, security researcher reports or other sources and converting that into material changes in your defensive stance is a key part of a modern defensive operation. Measure the success of your intelligence operation by how often it results in you making changes to your defensive setup – that is the goal.
For many years, we’ve warned that during periods of conflict, not everyone would stay on the sidelines. The speed at which this has occurred in this current conflict has, frankly, taken us by surprise. We assess that both Russian and Ukrainian governments have actively solicited otherwise unaffiliated actors to engage in attacks against their adversaries. We are highlighting this unsophisticated, unpredictable, and largely unknown set of actors so that customers who are fixated on the potential for top-tier state-sponsored attacks are not tripped up by an unsophisticated but highly motivated actor.
As our research continues, and as the global situation changes, we will continue to update our findings associated with the ongoing Russian invasion of Ukraine through our main blog here.




0 Comments